Azure Frontdoor WAF Anomaly Score Troubleshooting
There’s a unique identifier under the trackingReference that shows all the matches that have increased the anomaly score eventually causing it to be blocked.
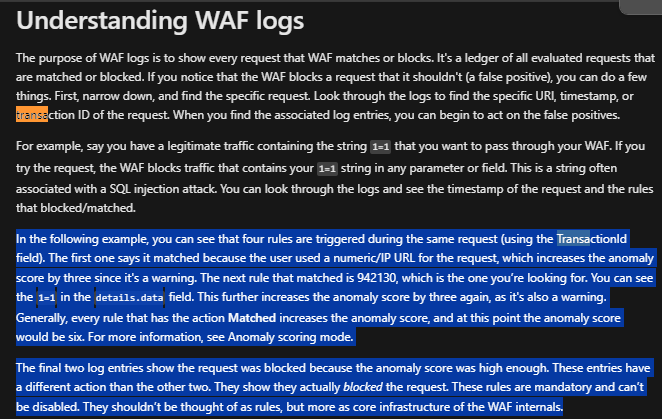
More details on how to query the information
The example query below I came up with should be more helpful in identifying which requests were blocked and then also showing the rules that were hit increasing the anomaly score. In the first section is finding all requests that were blocked, then joining the same table on those specific trackingIds so we can see the full lifetime of the request. The last “project” statement is reducing the columns for easier viewing.
AzureDiagnostics
| where ResourceProvider == “MICROSOFT.CDN”and Category == “FrontDoorWebApplicationFirewallLog”
| where action_s == “Block”
| summarize by trackingReference_s
| join (AzureDiagnostics
| where ResourceProvider == “MICROSOFT.CDN”and Category == “FrontDoorWebApplicationFirewallLog”
) on trackingReference_s
| project TimeGenerated, ruleName_s, clientIP_s, host_s, requestUri_s, details_msg_s, details_data_s, socketIP_s, policy_s, action_s, policyMode_s, details_matches_s,trackingReference_s